
Australians rely heavily on online banking, cloud storage, mobile apps, and digital services and with that comes an increasing risk of cyber attacks, data breaches, and unauthorised access. Data encryption techniques are a core defence strategy, helping individuals, businesses, and government agencies safeguard their information from prying eyes.
This guide breaks down what data encryption is, how it works, and the common techniques used to keep data secure across Australia’s digital landscape.
What Is Data Encryption?

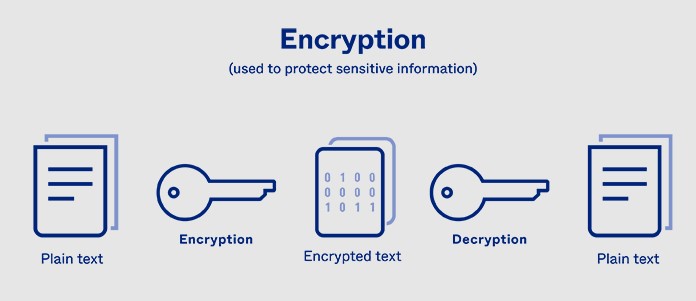
Data encryption is the process of converting readable information (plaintext) into an unreadable format known as ciphertext. Only users with the correct decryption key can convert the data back to its original form.
Encryption is used to protect:
- Personal details
- Banking and financial information
- Business records and intellectual property
- Health data
- Private communications
Encryption applies to data at rest (stored), data in transit (moving across networks), and even data in use (being processed).
Why Encryption Matters in Cybersecurity?
Cyber threats continue to rise in Australia, with ransomware, data breaches, and hacking attempts affecting businesses of all sizes. Strong data encryption techniques help:
- Prevent unauthorised access
- Protect data from cybercriminals
- Maintain confidentiality and trust
- Reduce the risk of data breaches
- Meet legal and compliance obligations, including the Privacy Act 1988 and the Australian Cyber Security Centre (ACSC) Essential Eight
Simply put: encryption is no longer optional it’s essential.
Key Data Encryption Techniques
There are several data encryption techniques used to secure information. Each has its own strengths and is suited to different cybersecurity needs.
Symmetric Encryption
How it works:
A single shared key is used to both encrypt and decrypt data.
Pros:
- Very fast and efficient
- Ideal for encrypting large volumes of data
- Low computational overhead
Cons:
The key must be shared between parties, creating a security risk if intercepted
Common algorithms:
- AES (Advanced Encryption Standard) – the global standard
- 3DES (Triple DES) – older and being phased out
- Blowfish and Twofish – widely used in open-source software
Where it’s used:
- Cloud storage
- Encrypted databases
- Secure backups
- File-level encryption
Asymmetric Encryption (Public-Key Cryptography)
How it works:
Uses two keys a public key to encrypt and a private key to decrypt.
Pros:
- More secure for sharing keys
- Private key never leaves the owner
- Ideal for digital signatures and authentication
Cons:
- Slower than symmetric encryption
- Not suitable for encrypting large files on its own
Common algorithms:
- RSA
- ECC (Elliptic Curve Cryptography) – efficient for mobile and IoT devices
Where it’s used:
- Secure email
- Digital certificates
- Website security (HTTPS)
Hashing
How it works:
Hashing converts data into a fixed-length string known as a hash. It cannot be reversed.
Pros:
- Excellent for verifying integrity
- Ideal for secure password storage
Common algorithms:
- SHA-256
- SHA-3
- Bcrypt
- Argon2 (recommended for modern security)
Where it’s used:
- Password hashing
- Verifying file downloads
- Blockchain applications
Hybrid Encryption
Modern cybersecurity systems combine both symmetric and asymmetric encryption to maximise security and efficiency.
How it works:
- Asymmetric encryption is used to securely exchange a symmetric key
- Symmetric encryption is then used to quickly encrypt the data
Where it’s used:
- HTTPS/TLS
- Online banking
- Secure messaging
- E-commerce platforms
Hybrid systems provide the best of both worlds: strong security with high performance.
Key Protocols and Tools That Use Encryption
These everyday technologies rely on strong data encryption techniques:
Transport Layer Security (TLS)
TLS is used to secure web traffic and online connections. You’ll know it’s active when you see the padlock icon in your browser.
It uses a hybrid system public-key encryption for the key exchange and symmetric encryption for the data transfer.
Virtual Private Networks (VPNs)
VPNs create encrypted tunnels between your device and the internet, protecting your activity from:
- Hackers
- Unsecured Wi-Fi networks
- ISP tracking
They’re widely used by remote workers, businesses, and travellers.
End-to-End Encryption (E2EE)
Only the sender and receiver can read the messages—no third party, not even the service provider.
Used in:
- Signal
- Facebook Messenger (optional)
Device & Disk Encryption
Modern phones and computers encrypt their storage automatically.
Examples:
- BitLocker (Windows)
- FileVault (Mac)
- Full-disk encryption on Android and iOS devices
If your device is lost or stolen, encryption keeps your data protected.
Cloud Encryption
Cloud providers encrypt data at rest and in transit.
However, businesses still need to manage keys properly to avoid exposure.
Advanced and Emerging Encryption Methods
As cyber threats evolve, so do encryption techniques.
- Homomorphic Encryption: Allows computations on encrypted data without revealing the raw information. Useful for secure cloud processing.
- Quantum-Resistant Encryption: Designed to protect against future quantum computing attacks which may break traditional algorithms like RSA.
- Zero-Knowledge Proofs (ZKPs): Used in privacy-focused blockchain technologies to verify information without revealing the data itself.
How Australian Businesses Can Implement Strong Encryption?
Here are practical steps for Aussie organisations:
- Encrypt all sensitive data using AES-256
- Use TLS 1.3 for secure data transmission
- Enable full-disk encryption on laptops and mobile devices
- Implement strong password hashing (Argon2, Bcrypt)
- Regularly rotate encryption keys and certificates
- Use VPNs for remote staff
- Follow ACSC Essential Eight guidelines
- Conduct regular cybersecurity audits
Strong encryption is one of the most effective ways to reduce cybersecurity risks and protect business continuity.
Common Encryption Mistakes to Avoid
To ensure maximum protection, steer clear of these errors:
- Using outdated or broken algorithms like MD5 and SHA-1
- Poor encryption key management
- Failing to encrypt backups
- Misconfigured TLS or VPN settings
- Relying on encryption alone without firewalls or access controls
Conclusion
Data encryption techniques are at the heart of strong cybersecurity. Whether you’re protecting personal information, securing business systems, or safeguarding client data, encryption provides a powerful defence against Australia’s growing cyber threats.
By understanding how encryption works and implementing it correctly you can significantly reduce the risk of data breaches and maintain trust in an increasingly digital world.
Call us on 1300 832 639 or simply search “Exceed ICT” on Google Maps to find a location near you and connect with our team today.
We also provide
Telecoms Expense Management, Device Deployment, Fleet management, Telstra enterprise Mobility, Telstra mobility Managed Services.
Improve Business Core values, Business Consulting, Network Management, Telstra Expense Management and many more Services.


