
A Guide to Data Encryption Techniques
 Are you worried about the security of your sensitive data? In today’s world, where data breaches and cyberattacks are on the rise, it’s essential to protect your data with encryption. Encryption is a technique that converts your data into an unreadable format, making it impossible for hackers to decipher. This guide will help you understand the different types of encryption techniques and how they can help you secure your data.
Are you worried about the security of your sensitive data? In today’s world, where data breaches and cyberattacks are on the rise, it’s essential to protect your data with encryption. Encryption is a technique that converts your data into an unreadable format, making it impossible for hackers to decipher. This guide will help you understand the different types of encryption techniques and how they can help you secure your data.
In this digital age, data is one of the most valuable assets for individuals and businesses alike. From personal information to financial data, we store all kinds of sensitive information on our devices. However, with the increasing amount of cyber threats, it has become imperative to secure this data. Data Encryption techniques are the key to data protection. This guide will provide you with an in-depth understanding of data encryption techniques and their importance in data protection.
Types of Data Encryption Techniques
Encryption techniques can be broadly classified into two categories: symmetric and asymmetric encryption.
Symmetric Encryption
Symmetric encryption, also known as shared secret encryption, uses the same secret key for both encryption and decryption. This key is shared between the sender and the receiver of the encrypted data. The most common symmetric encryption algorithms are Advanced Encryption Standard (AES), Data Encryption Standard (DES), and Triple DES.
Asymmetric Encryption
Asymmetric encryption, also known as public-key encryption, uses a pair of keys: a public key and a private key. The public key is used for encryption, and the private key is used for decryption. The most common asymmetric encryption algorithms are RSA, Elliptic Curve Cryptography (ECC), and Digital Signature Algorithm (DSA).
Importance of Data Encryption Techniques
Data Encryption techniques plays a crucial role in data protection.
Here are some reasons why encryption is important:
Protection against unauthorized access: Encryption makes it impossible for unauthorized users to access your data.
Compliance with regulations: Many industries have regulations that require the use of encryption to protect sensitive data.
Protection against data breaches: Encrypted data is useless to hackers, even if they manage to steal it.
How Data Encryption techniques Works
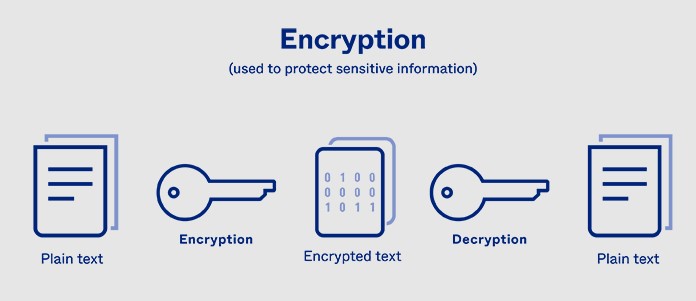 Encryption involves converting your data into an unreadable format that can only be read by authorized parties. The encryption process involves the use of a key, which can be a shared secret key in the case of symmetric encryption, or a pair of keys in the case of asymmetric encryption.
Encryption involves converting your data into an unreadable format that can only be read by authorized parties. The encryption process involves the use of a key, which can be a shared secret key in the case of symmetric encryption, or a pair of keys in the case of asymmetric encryption.
Types of Attacks on Encrypted Data
While encryption techniques provide an effective way to protect your data, they are not foolproof. Here are some types of attacks that can be launched on encrypted data:
Brute-force attacks: These attacks involve trying all possible combinations of keys until the correct key is found.
Dictionary attacks: These attacks involve using a list of words or phrases to guess the encryption key.
Man-in-the-middle attacks: These attacks involve intercepting the communication between the sender and the receiver and altering the data in transit.
Best Practices for Encryption
To ensure the effectiveness of encryption techniques, it is essential to follow best practices. Here are some best practices for encryption:
Use strong encryption algorithms: Use strong encryption algorithms such as AES and RSA to ensure the security of your data.
Protect your encryption keys: Keep your encryption keys secure and avoid sharing them with unauthorized parties.
Use two-factor authentication: Use two-factor authentication to add an extra layer of security to your encrypted data.
Frequently Asked Questions
Q1. What is the difference between symmetric and asymmetric encryption?
Symmetric encryption uses the same key for both encryption and decryption, while asymmetric encryption uses a pair of keys: a public key and a private key.
Q2. Is encryption 100% secure?
No, encryption is not 100% secure. While encryption can provide effective protection against unauthorized access, it can be vulnerable to certain types of attacks. However, by following best practices and using strong encryption algorithms, you can significantly reduce the risk of a successful attack.
Q3. Can encrypted data be decrypted?
Encrypted data can be decrypted if the correct key is used. However, if the encryption key is kept secure and not shared with unauthorized parties, the data will remain secure.
Q4. What are the most common encryption algorithms?
The most common symmetric encryption algorithms are Advanced Encryption Standard (AES), Data Encryption Standard (DES), and Triple DES. The most common asymmetric encryption algorithms are RSA, Elliptic Curve Cryptography (ECC), and Digital Signature Algorithm (DSA).
Q5. Is it necessary to encrypt all data?
While it’s not necessary to encrypt all data, it’s essential to encrypt sensitive data such as personal information, financial data, and confidential business information. Additionally, many industries have regulations that require the use of encryption for certain types of data.
Q6. Can encryption slow down data transfer?
Encryption can slow down data transfer, especially if large amounts of data are being transferred. However, the slowdown is usually minimal, and the benefits of encryption outweigh the minor inconvenience.
Encryption techniques are essential for protecting sensitive data in today’s digital age. By using strong encryption algorithms, keeping encryption keys secure, and following best practices, you can significantly reduce the risk of a successful attack. While encryption is not 100% secure, it provides an effective way to protect your data against unauthorized access and data breaches.
You may also like to know more about
- Ultimate Guide to Cyber Security.
- Boost Your Cyber Security Awareness: A Comprehensive Guide.
- Explore the strong Endpoint Security.
- Protect Your Data with Mobile Data Security Measures.
- How to Secure Business with Mobile Security Solutions.
Stay connected with EXCEED ICT
Stay connected with EXCEED ICT by joining our social networks (given at footer). Get the latest updates, news, and tips for enterprise device deployment. Follow us on Twitter, Facebook, and LinkedIn for the best enterprise device deployment solutions.
Help us to improve our enterprise by rating us on Google Maps. Your feedback and comments are valuable to us and will be used to make our services even better.
Thanks visiting.



